New approaches to virus protection
 The Internet Storm Center (ISC) has made the effort to list the hash values of around 40 million programs contained in the US National Software Reference Library (NSRL) in a database in such a way that they can be retrieved via a web front end. This potentially presents an alternative to anti-virus scanners searching for malicious code.
The Internet Storm Center (ISC) has made the effort to list the hash values of around 40 million programs contained in the US National Software Reference Library (NSRL) in a database in such a way that they can be retrieved via a web front end. This potentially presents an alternative to anti-virus scanners searching for malicious code.
The US NIST maintains a comprehensive collection of known programs and generates hash values of the files they contain. These allow the files to be identified conclusively. At present, the collection is mainly used for excluding standard files in forensic investigations. However, it could also be used for avoiding problems such as false alarms triggered by standard files.
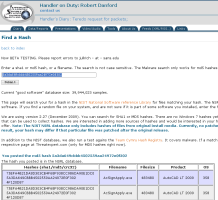
![]() The ISC now allows users to search for the hashes of known files.
For example, on Monday anti-virus vendors sounded a false alarm saying that a file belonging to AutoCAD, AcSignApply.exe contained mailware; If Avira, Kaspersky, F-Secure and other anti-virus vendors had queried the NIST database beforehand they would have known that the NIST lists the AcSignApply.exe file as a known AutoCAD file with an MD5 hash value of 5A3DA649CBBB4502559AA24972E0F302. While this is no automatic guarantee that the file doesn't include some sort of back door, it would at least have allowed the vendors to avoid a false alarm apparently based on very weak evidence.
The ISC now allows users to search for the hashes of known files.
For example, on Monday anti-virus vendors sounded a false alarm saying that a file belonging to AutoCAD, AcSignApply.exe contained mailware; If Avira, Kaspersky, F-Secure and other anti-virus vendors had queried the NIST database beforehand they would have known that the NIST lists the AcSignApply.exe file as a known AutoCAD file with an MD5 hash value of 5A3DA649CBBB4502559AA24972E0F302. While this is no automatic guarantee that the file doesn't include some sort of back door, it would at least have allowed the vendors to avoid a false alarm apparently based on very weak evidence.
Beyond that, the ISC's Johannes B. Ullrich also considers it possible for such "whitelisting" to replace traditional anti-virus concepts particularly in controlled corporate environments. Current AV concepts are based on covering all potentially harmful eventualities ("enumerating badness"), which is becoming increasingly difficult. This makes a whitelisting approach, which only allows approved applications naturally attractive.
Ullrich says that the problem with this approach is that even administrators don't usually know which software should be running on a system and which shouldn't. Programs changing via updates are an added complication. He adds that a less stringent whitelisting approach such as the one based on the NSRL database, supplemented by specific hashes, could bring truly practicable solutions within reach.
The ISC's database accepts hash queries as well as file name queries, but it doesn't currently include any Windows 7 files. Over time, there are plans for the database to include additional information from other clearly defined trustworthy sources. The ISC already returns potential hits in Team Cymru's Malware Hash Registry. DNS lookup queries are also being discussed.
(djwm)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








