Microsoft patches URI security vulnerability
As announced, the Redmond-based software giant issued two Security Bulletins for November's Patch Tuesday. One of the updates resolves a vulnerability in the way that the Windows shell handles specifically crafted URIs passed to it by other applications, and the other resolves a security vulnerability in Windows DNS Servers.
After learning almost a month ago that as well as third party applications Microsoft products such as Outlook are also affected by this vulnerability via crafted URIs such as mailto:%xx../../../../../../../../../windows/system32/calc.exe".cmd, the company announced it would be issuing a patch and is now offering it with the update associated with Security Bulletin MS07-061. If you still have an unofficial patch installed on your computer, you should remove it and install the official patch.
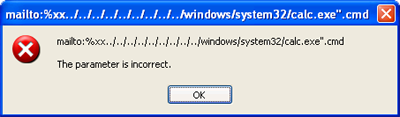
After installing Update MS07-061 the specially crafted URIs merely generate an error message.
Microsoft explains in the Security Bulletin that the critical vulnerability can be traced back to the way the Windows shell handles invalid URIs. However, the flaw only occurs on systems using Internet Explorer 7. The vulnerability has already been exploited using specially crafted PDF files that install malicious software when opened using Adobe Reader. The update replaces the vulnerable file, Shell32.dll, with an updated version. Microsoft has determined that the vulnerability affects Windows XP SP2, Windows XP Professional x64 Edition with and without SP2, Windows Server 2003 SP1 or SP2, Windows Server 2003 x64 Edition and Windows 2003 Server x64 Edition SP2, and Windows Server 2003 with SP1 or SP2 for Itanium-based systems.
The second Security Bulletin, with a maximum severity rating of Important, resolves a vulnerability in Windows DNS Servers. Low entropy under Windows 2000 Server and Windows Server 2003 in the generation of the transaction-ID could allow an attacker to guess a correct transaction-ID and to send specially crafted responses to DNS requests, thereby spoofing or redirecting Internet traffic from legitimate locations. A similar vulnerability in DNS Server BIND 8 ratified its end of lifecycle back in August.
Microsoft also announced in its Microsoft Security Response Center Blog that it is also re-releasing an updated version of Security Bulletin MS07-049, which addresses a security vulnerability in Virtual PC and Virtual Server. The vendor has merely made a change to the installer code, because installation sometimes failed in older versions. If you have already successfully installed the update, you do not need to reinstall it. As in previous months, Microsoft has also released an updated version of its Malicous Software Removal Tool (MSRT), which checks computers for infections by specific, prevalent malicious software and helps remove any infection found.
- Microsoft Security Bulletin Summary for September 2007
- Vulnerability in Windows URI Handling Could Allow Remote Code Execution Microsoft security bulletin
- Vulnerability in DNS Could Allow Spoofing, Microsoft security bulletin
(mba)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








