Microsoft and Symantec collaborate to disable click-fraud botnet
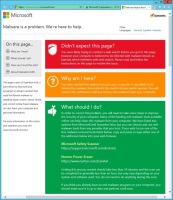
![]() As the C&C servers have been switched off, victims are now being redirected to an information page
As the C&C servers have been switched off, victims are now being redirected to an information page
Source: Microsoft
Microsoft and Symantec worked with US and Spanish officials to take down the Bamital click-fraud botnet which has been operating since at least 2009 and was, at one point, made up of more than 1.8 million compromised systems. According to a report in Kaspersky Lab's threatpost, infected computers would have their searches intercepted and redirected to the botnet operators' servers, along with the search terms that were originally entered. This would allow the botnet operators to sell the clicks of these users to other criminals and redirect traffic to their web sites.
The botnet's distribution apparently peaked at the end of 2011 and the beginning of 2012. Microsoft filed a lawsuit against the botnet's operators, who turned out to be based in Russia and Eastern Europe, on 31 January 2013 and was granted a court order to go after the botnet's command & control (C&C) servers a few days later. On 6 February, Microsoft and officials from the US Marshals Service seized data and evidence from web hosting companies in New Jersey and Virginia to disrupt the botnet's operations. Symantec, working with Spanish officials, including the Guardia Civil, analysed a C&C server of the botnet and found that it was receiving 120,000 connections a day from more than 200 countries.
Victims were infected through drive-by attacks or malware bundled with applications downloaded from peer-to-peer networks. The drive-by attacks were mostly carried out from compromised pornography web sites. The Phoenix exploit pack and other methods were used to infect machines with the Bamital trojan, which once installed, set a browser cookie with the name "yatutuzebil", Russian for "I was already here". The Bamital trojan comprised three parts: a command & control module, a component that hijacked the search engine results on a user's machine and a third module that created traffic on web sites without the user's interaction. This third module "clicked" on web site links and ads in the background of existing web sessions to generate revenue.
Microsoft said the operation was their sixth botnet takedown in the last three years and its second such co-operation with Symantec. Kelihos, Nitol and some Zeus botnets are among those previously taken down by Microsoft actions.
(fab)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








