Malware spread through fake 'Barack Obama resigns' websites
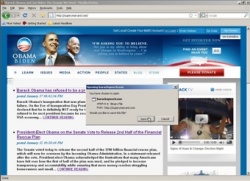
![]() An example of a fake Barack Obama site and malware download lure
According to a press release from PandaLabs and originally noted on the companies blog, over 40 websites are exploiting Barack Obama's presidential inauguration. The sites are spoof web pages that appear to be from Obama's official campaign, reporting that Obama has resigned as President of the United States. These sites claim that the decision was "motivated by the President-elect's inability to save America from the global economic downturn." One of the headlines used was "Barack Obama has refused to be a President."
An example of a fake Barack Obama site and malware download lure
According to a press release from PandaLabs and originally noted on the companies blog, over 40 websites are exploiting Barack Obama's presidential inauguration. The sites are spoof web pages that appear to be from Obama's official campaign, reporting that Obama has resigned as President of the United States. These sites claim that the decision was "motivated by the President-elect's inability to save America from the global economic downturn." One of the headlines used was "Barack Obama has refused to be a President."
PandaLabs states that the attacks seem to be coming from China, as all of the discovered domains have been bought by a Chinese company called Xinnet Technology Corporation, an organisation with a previous record of malware attacks. The sites attempt to get users to download executable files such as "barachspeech.exe" and then run them to install the Ikmas.A.worm (W32/Iksmas.A.worm). This worm attempts to spread to as many computers as possible to build a botnet. According to PandaLabs the malware botnet is "set up to financially exploit computer users" by stealing online bank and account details.
This is not the first time that President-Elect Barack Obama's name has been used to spread Malware. In November 2008 a Trojan (Spyforms.BQ) was distributed in an e-mail message, stating that Barack Obama had become the 44th President of the United States.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








