Lost iPhone = lost passwords
 Fraunhofer researchers Jens Heider and Matthias Boll have succeeded in reading saved passwords from an iPhone despite it being locked with a passcode. This means that a lost or stolen iPhone continues to represent a serious security problem even with the latest iPhone version.
Fraunhofer researchers Jens Heider and Matthias Boll have succeeded in reading saved passwords from an iPhone despite it being locked with a passcode. This means that a lost or stolen iPhone continues to represent a serious security problem even with the latest iPhone version.
The two researchers from the Fraunhofer Institute for Secure Information Technology (SIT) utilise precisely the scenario previously outlined in tests on online banking apps ![]() by The H's associates at heise Security. By using a modified jailbreak, they gain access to the iPhone 4 (running iOS 4.2.1) file system and install an SSH server, which is launched automatically on booting. Since jailbreaks which are active during booting are available even for the latest iOS version, a passcode is not able to protect against this scenario. And if you can login to the system once it is active, encryption is not going to help either, since the system decrypts all files which do not use additional security automatically.
by The H's associates at heise Security. By using a modified jailbreak, they gain access to the iPhone 4 (running iOS 4.2.1) file system and install an SSH server, which is launched automatically on booting. Since jailbreaks which are active during booting are available even for the latest iOS version, a passcode is not able to protect against this scenario. And if you can login to the system once it is active, encryption is not going to help either, since the system decrypts all files which do not use additional security automatically.
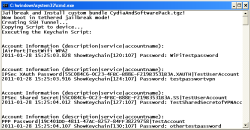
![]() A simple script can serve up iPhone passwords on a silver platter.
A simple script can serve up iPhone passwords on a silver platter.
Source: Fraunhofer SIT
Heider and Boll's next step involved getting to the saved passwords. Although these are stored in encrypted form in the 'keychain', applications are able to access them in unencrypted form – iOS helpfully decrypts them. Consequently, it is not necessary to crack the encryption or determine the key used. Instead, the researchers copied a homemade app onto the jailbroken iPhone, which then served up the passwords on a silver platter. The technique also enabled them to obtain saved passwords for Wi-Fi networks and VPNs.
Not all data was accessible however – Apple has added extended security features to iOS 4, which allow apps to improve the security of data on the file system and in the keychain by assigning them attributes such as NSFileProtectionComplete and kSecAttrAccessibleWhenUnlocked. These attributes cause the data to be encrypted, so that the iPhone cannot decrypt them without the user's passcode.
At present, however, few applications utilise this feature, which is only available on iOS 4 – even Apple's own apps barely make use of it. A significant exception is the Mail app, which uses the kSecAttrAccessibleWhenUnlocked attribute when saving passwords for accessing email. The password stealing demo was unable to decrypt these passwords. Interestingly, the password was not protected when, for example, a Google Mail account was addressed as an MS Exchange account. The researchers were also unable to access passwords saved in Safari.
Users should not, therefore, rely on encryption of data on the iPhone. Heider and Boll's paper 'Practical Consideration of iOS Device Encryption Security![]() ' concludes that, should an iPhone fall into the wrong hands, owners should change all passwords which are stored on the lost iPhone ASAP.
' concludes that, should an iPhone fall into the wrong hands, owners should change all passwords which are stored on the lost iPhone ASAP.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








