Lost+Found: FileVault2, 1-day Flash exploit, WPA cracking, airport insecurity and cryptocat
 Too short for news, too good to lose; Lost+Found is a roundup of useful security news. This time: analysing Apple's FileVault2 encryption software, 1-day Flash exploit, cracking WPA with Amazon EC2, inadvertently circumventing airport security, and Cryptocat.
Too short for news, too good to lose; Lost+Found is a roundup of useful security news. This time: analysing Apple's FileVault2 encryption software, 1-day Flash exploit, cracking WPA with Amazon EC2, inadvertently circumventing airport security, and Cryptocat.
-
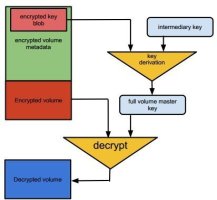
 The encryption used in FileVault2 is based on AES-XTS
The encryption used in FileVault2 is based on AES-XTS
Source: Choudary, Metz, Gröbert Security researchers have performed an extensive analysis of Apple's FileVault2 hard drive encryption program in Mac OS X 10.7 Lion and have published their findings. While their report doesn't explicitly detail security problems, it does document the complete architecture of Apple's proprietary encryption software. This information will be particularly helpful for those developing forensic tools for mounting FileVault-encrypted volumes such as libfvde. The researchers' findings can be found in a 14 page paper entitled "Infiltrate the Vault: Security Analysis and Decryption of Lion Full Disk Encryption ".
".
- Only one day after Adobe released its last round of updates, malicious Word documents that claimed to contain information about the next iPhone began circulating. These files exploited one of the publicised holes in Flash Player (CVE-2012-1535) to infect systems with malicious code.
- What can you do with the 750 hours of computing time per month that Amazon offers its EC2 cloud users for the first year? Blogger Leigh Bicknell has used it to crack WPA keys. Although the individual computers are quite slow, the bundled CPU power from 140 simultaneous computer instances allowed Bicknell to go through a respectable 28,000 keys per second – roughly equivalent to the power of a fast graphics card.
- The multi-million dollar security system used by New York's John F Kennedy airport failed a recent unexpected security test when it didn't spot a man wearing a bright yellow life jacket. Daniel Castello was jet skiing near the airport when he ran out of fuel. To get help, he swam ashore, climbed the eight foot security fence that surrounds the airport, and crossed two runways without being spotted. Castello then walked up to a Delta employee on the tarmac and asked for help, at which point he was arrested by the Port Authority for trespassing.
- After Wired magazine published a euphoric article on the Cryptocat encrypting chat program, security specialist Chris Soghoian was one of the first to warn of indiscriminate reviews of programs whose users could be putting their lives on the line. Later, he got help from cryptography guru Bruce Schneier, who expressed serious concerns regarding the Cryptocat concept.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








