Kaspersky: Number of Macs infected by Flashback drops to 30,000 - Update
![]() The number of Flashback infected systems has dropped significantly since the beginning the month
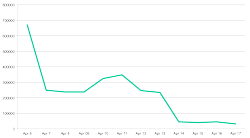
The number of Flashback infected systems has dropped significantly since the beginning the month
Source: Kaspersky Lab
According to a report, security specialist Kaspersky Lab says that the number of systems infected with the Flashback trojan has dropped from more than 600,000 at the start of the month to just 30,000. That figure is substantially lower than Symantec's estimate of 140,000 from earlier in the week.
None of the security firms currently know who is behind the trojan, which is sometimes also referred to as Flashfake. In a post on the company's Securelist web site, Kaspersky Lab's Kurt Baumgartner speculates that a group of eastern European cyber criminals is likely behind the malware: "There are known groups from the region that have succeeded at wringing ad revenues from traffic hijacking." He goes on to note that the company doesn't believe that the criminals are targeting sensitive data, but rather that they are most likely "looking to make a multitude of small financial gains".
The Flashback malware and its variants re-emerged in February of this year, exploiting a previously unpatched Java vulnerability in Mac OS X to infect users' systems when visiting a specially crafted web site. Following the initial outbreak, Apple released updates to its Java implementation for Mac OS X 10.6 Snow Leopard and 10.7 Lion that close the hole being exploited by Flashback. The company later published an updated version of the Java update that also included a Flashback removal tool for infected systems, as well as a standalone removal removal tool for Mac OS X 10.7 users without Java installed.
Update: Dr Web, the Russian company who published the original 600,000 estimate says that reports of a drop in infections are incorrect saying in a blog posting that there are, according to its sinkhole monitoring, over 560,000 systems still infected. The company suggests that the variation in the figures is because after connecting to the Dr Web controlled server, the bots are connecting to a C&C server controlled by an unidentified third party. Because that server doesn't close the connection, the bots are going into a sleep mode awaiting a reply and not moving on to other C&C server addresses which are being monitored by other security vendors.
See also:
- Worth Reading: An analysis of the Flashback/Flashfake trojan, a report from The H.
- Mozilla blocklists Java on older Mac OS X systems, a report from The H.
- New Mac malware exploits old Java hole, a report from The H.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








