Internet Explorer's Protected Mode can be bypassed
 With Internet Explorer 7 and Windows Vista, Microsoft introduced a Protected Mode. This feature is designed to protect computers against attacks exploiting vulnerabilities in IE extensions or in the browser itself and prevent the injection of malicious software.
With Internet Explorer 7 and Windows Vista, Microsoft introduced a Protected Mode. This feature is designed to protect computers against attacks exploiting vulnerabilities in IE extensions or in the browser itself and prevent the injection of malicious software.
Researchers from Verizon Business have now described![]() a way of bypassing Protected Mode in IE 7 and 8 in order to gain access to user accounts. The technique requires a vulnerability that allows the execution of malicious code in the browser or in a browser extension. Although the malware will initially only run in the browser's Low Integrity Mode, it can start a web server on the computer that will respond to requests on any port of the loopback interface. By calling the IELaunchURL() function, an attacker can instruct IE to load a URL from this web server, for instance "http://localhost/exploit.html". Localhost is generally part of IE's Local Intranet Zone and, by default, Protected Mode is disabled for content from this zone.
a way of bypassing Protected Mode in IE 7 and 8 in order to gain access to user accounts. The technique requires a vulnerability that allows the execution of malicious code in the browser or in a browser extension. Although the malware will initially only run in the browser's Low Integrity Mode, it can start a web server on the computer that will respond to requests on any port of the loopback interface. By calling the IELaunchURL() function, an attacker can instruct IE to load a URL from this web server, for instance "http://localhost/exploit.html". Localhost is generally part of IE's Local Intranet Zone and, by default, Protected Mode is disabled for content from this zone.
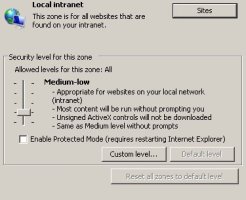
![]() In IE8, by default, protected mode for all the local intranet sites is disabled.
Executing the exploit a second time in this situation allows arbitrary code to be launched at "Medium Integrity" level. Attackers will then be able to access a user's account and permanently install arbitrary software on the computer.
In IE8, by default, protected mode for all the local intranet sites is disabled.
Executing the exploit a second time in this situation allows arbitrary code to be launched at "Medium Integrity" level. Attackers will then be able to access a user's account and permanently install arbitrary software on the computer.
To prevent the described attack, the researchers recommend that users keep the number of sites in IE's local intranet zone to a minimum and enable Protected Mode for all browser zones.
(trk)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








