Indiscrete web browsers assist de-anonymisation
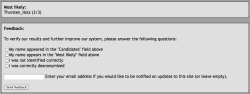
![]() Using the information entered by visitors, the research team hopes to find out how reliable the test really is.
A test on browser fingerprinting by the Electronic Frontier Foundation (EFF) has shown how uniquely identifiable a user's browser is on the web. What that test is unable to do is to identify individual users. This, however, is the goal of an experiment by the International Secure Systems Lab (Isec Lab). Originally founded by the Vienna University of Technology (TUV), Isec Lab is now a collaborative venture between TUV, Eurécom and the University of California in Santa Barbara. The test makes use of Xing, a platform widely-used in Europe on which many millions of users have published profiles.
Using the information entered by visitors, the research team hopes to find out how reliable the test really is.
A test on browser fingerprinting by the Electronic Frontier Foundation (EFF) has shown how uniquely identifiable a user's browser is on the web. What that test is unable to do is to identify individual users. This, however, is the goal of an experiment by the International Secure Systems Lab (Isec Lab). Originally founded by the Vienna University of Technology (TUV), Isec Lab is now a collaborative venture between TUV, Eurécom and the University of California in Santa Barbara. The test makes use of Xing, a platform widely-used in Europe on which many millions of users have published profiles.
The test essentially exploits the fact that many Xing users are identifiable by their membership of various groups. According to Thorsten Holz, one of the researchers who designed the experiment, there are very few people on any social network who belong to exactly the same groups. A 'group fingerprint' could thus allow websites to identify previously anonymous visitors.
However, a little spadework is required in order to access this information. The researchers have crawled as many Xing groups and their associated forums as possible in order to obtain an overview of Xing users and to collect URLs for the test proper. They have found roughly 1.8 million users organised into around 7,000 groups.
The second step is the actual test. Using special calls by the website within the browser, a website can determine whether a specific site on another server has previously been viewed by a visitor (this technique is known as history stealing). This enables the test to determine which group pages a user has visited. For each group found, the test now checks whether the current visitor is a particular member of the group (on the forum) by again checking through the previously collected URLs. The fact that social networks contain unique URLs, such as personal profile pages, should also make it possible to more or less unambiguously identify someone.
According to the report, in order to determine a user's 'group fingerprint', the test only needs to check around 92,000 URLs, which takes less than a minute. By correlating the data, it is possible to further tighten the circle so that frequently only a single user remains. Isec Labs states that initial practical tests have given good results, but notes that so far only 30 tests have been carried out. A quick test by the The H's associates at heise Security found that in two cases the experiment failed to return any results – although the users were members of Xing groups, they were either not active in the forums or had recently cleared their browser history. In one case, however, the test returned two names, one of which was the user's.
According to Holz, other large social networks such as LinkedIn and Facebook could also be used for this type of test, although the shear size of these networks and the resulting data volumes would present a problem. He adds that the team has, using two computers, already found more than 40 million profiles on Facebook and that, with better equipment, it would probably be possible to crawl all of Facebook.
Gilbert Wondracek, Thorsten Holz, Engin Kirda and Christopher Kruegel describe the principles of the test in full in "A Practical Attack to De-Anonymize Social Network Users"![]() . The paper also describes practical remedies for protecting against this kind of de-anonymisation attack, all of which are aimed at hampering history stealing. On the server-side, operators could insert random tokens into URLs, making it much more difficult to probe URLs at a later date. Client-side, users can block access to browser history by, for example, visiting certain sites in incognito mode, using protective plug-ins such as NoScript for Firefox or regularly clearing their history.
. The paper also describes practical remedies for protecting against this kind of de-anonymisation attack, all of which are aimed at hampering history stealing. On the server-side, operators could insert random tokens into URLs, making it much more difficult to probe URLs at a later date. Client-side, users can block access to browser history by, for example, visiting certain sites in incognito mode, using protective plug-ins such as NoScript for Firefox or regularly clearing their history.
The authors have also made the test publicly available. The test requires users to reveal some information on how much they use Xing and groups. After completing the test, a second form asks users to reveal whether they have been (uniquely) identified. Holz points out that none of the data collected is stored or used for other purposes, and that the group is merely interested in voluntary feedback from readers/testers.
See also:
- EFF demonstrates a browser's "finger print", a report from The H.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








