ICS-CERT warns of increasing threat to industrial control systems
 Attacks on industrial control systems are on the rise: the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) has issued a warning
Attacks on industrial control systems are on the rise: the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) has issued a warning![]() , which has been reiterated by the German Federal Office for Information Security (BSI). Special tools and search engines make attacks on systems and devices in infrastructures such as electricity grids simple even for inexperienced attackers.
, which has been reiterated by the German Federal Office for Information Security (BSI). Special tools and search engines make attacks on systems and devices in infrastructures such as electricity grids simple even for inexperienced attackers.
Tools aimed at cracking digital control systems from companies such as GE, Rockwell Automation, Schneider Electric and Koyo were released earlier this year. Tools for CoDeSys software from German company 3S Software have also recently made an appearance. These tools lower the barriers for attackers by more or less removing the need for specialist knowledge in order to carry out an attack.
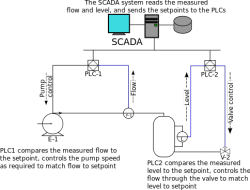
![]() The principle behind a SCADA system
The principle behind a SCADA system
Source: Wikipedia
Specialist search engines such as the Shodan Computer Location Service and the Every Routable IP Project (ERIPP) are also making life easier for attackers. One team of researchers told ICS-CERT that they had used Shodan to discover more than 500,000 unsecured devices which use SCADA and other industrial control systems (ICS). In Germany, awareness of the problem is reportedly good. Participants in a discussion held by the CAST Forum![]() were nonetheless unanimous that banning SCADA systems or factories from being connected to the internet would not be helpful – the benefits are simply too great.
were nonetheless unanimous that banning SCADA systems or factories from being connected to the internet would not be helpful – the benefits are simply too great.
The absence or inadequacy of access controls represent a further security risk. The BSI told The H's associates at heise Security that this is due to the need for systems to be operable around the clock. A piece of machinery has to continue to be able to be administered decades down the line, when staff members responsible for it within a company may have already come and gone. According to a BSI spokesman, "This is why many manufacturers have hard-coded access data, in order to provide a mechanism for resetting access data in the event that it is lost and to ensure access to machinery." This fallback position also provides attackers with a route into these systems.
ICS-CERT is advising businesses to audit their systems to check for security vulnerabilities. Owners and operators should not shy away from using Shodan and ERIPP to search for their own devices. This will also find any devices which they might have assumed were not even connected to the internet. In principle, these systems should only be connected to the web when absolutely necessary and should be protected behind a firewall and have strong passwords. Control system networks and company networks should be isolated from each other. Companies should also have their security systems externally audited.
ICS-CERT is part of the United States Computer Emergency Readiness Team (US-CERT), an agency of the Department of Homeland Security, and has specific responsibility for the security of industrial control systems. In Germany, the Federal Office for Information Security (BSI) fulfils a similar role, encompassing in particular "collaboration with manufacturers, integrators and operators."
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








