ICQ vulnerable to account theft - Update

In security advisories for ICQ and the ICQ web site, security researcher Levent Kayan warns that both the ICQ instant messenger for Windows and the ICQ web site contain vulnerabilities that potentially allow attackers to take control of a user's ICQ account. According to Kayan ICQ doesn't adequately check user's profile information and fails properly to analyse status messages, which can be freely chosen by users, to see if they contain executable code. Kayan recently discovered a similar hole in the Skype client.
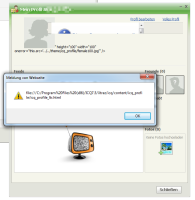
![]() A cross-site scripting hole enables attackers to deposit JavaScript code in their ICQ profiles.
A cross-site scripting hole enables attackers to deposit JavaScript code in their ICQ profiles.
If the victim opens the attacker's profile in the ICQ client or on the ICQ web site, the embedded JavaScript code stored on the ICQ server will be executed. This can allow attackers, for example, to steal victims' cookies and take control of their sessions. The script code appears to be executed in a local context: therefore, attackers can potentially also execute applications and read the user's local files.
Such an attack is called a persistent cross-site scripting attack; the attacker manages to place JavaScript code on a server that will be executed on the victim's machine when a particular web site is visited or a particular application is used. When asked by The H's German associates at heise Security, ICQ's press office didn't want to comment on the problem. heise Security managed to reproduce the problem with the current version 7.5 of ICQ under Windows 7.
Update: ICQ's PR company has told heise Security that the developers have identified the problem and are "well on the way" to fixing it.
(ehe)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








