Hackers claim to have beaten Xbox 360 security
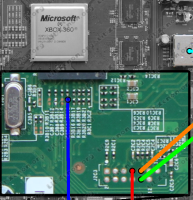
![]() Unable to bypass the Xbox 360's software security, the hackers sent interference signals to the console's hardware PCB
Unable to bypass the Xbox 360's software security, the hackers sent interference signals to the console's hardware PCB
Source: GliGli
Over the weekend, hackers GliGli and Tyros published a "Reset Glitch Hack" and a YouTube video showing how they succeeded in bypassing the security system on Microsoft's Xbox 360 game console to inject and execute their own code. In contrast to previous attacks, which either targeted the drives or exploited bugs in game software, the new attack targets the CPU and, according to the hackers, cannot be blocked by future software updates from Microsoft.
To bypass the Xbox 360's security, the hackers slowed down the CPU speed during boot. On the slim model, they achieved this by using an externally accessible HANA chip bus (12C) to overwrite the divider registers in the clock generator. With the clock speed slowed, they used a soldered PCB to send a 20 nanosecond pulse to the reset circuit at a specific time point. According to their report, this did not cause the CPU to reboot the system. They then restored the normal CPU clock speed. The hackers claim that this technique can be used to modify a command to compare memory areas (memcmp). With a little bit of luck, this in turn causes the Xbox to fail to properly check the bootloader signature, allowing the hackers to run their own bootloader.
Checks on revocation fuses are no longer performed for this bootloader, meaning that the hack cannot be blocked by a software update. In the video, the hackers launch a Linux loader (Xell) and a Nintendo 64 (N64) emulator. The attack is reported to run regardless of the installed firmware and dashboard versions. It does, however, take an average of four attempts for the reset pulse to achieve the desired effect. The new slim console model and the most recent version of the older 'fat' model (Jasper) are both vulnerable. The attack has not, however, been tested on first generation Xbox 360 hardware with a 175 watt power supply (Xenon, Falcon).
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








