Google researcher discloses zero-day exploit for Windows
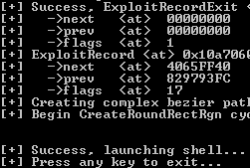
![]() It took a few goes, but the exploit was eventually able to provide a guest user with system privileges
It took a few goes, but the exploit was eventually able to provide a guest user with system privileges
Google security expert Tavis Ormandy has discovered a security vulnerability in Windows which can be exploited by any user on the system to obtain administrator privileges. Rather than reporting the vulnerability to Microsoft, he posted details to the Full Disclosure security mailing list in mid-May and has now published an exploit to the same mailing list.
Ormandy is a familiar figure in the security world. In recent years, the security expert has discovered many different vulnerabilities. He has also been known to take the shortest route when it comes to sharing information on vulnerabilities he has discovered: full disclosure, meaning rapid publication without informing the organisation behind the vulnerable software beforehand.
With this latest vulnerability, Ormandy once more opted for full disclosure on the mailing list of the same name. After discovering a bug in the Windows kernel's EPATHOBJ::pprFlattenRec function, he wrote to the list: "I don't have much free time to work on silly Microsoft code" and solicited ideas on how to successfully exploit the bug. With the help of user progmboy, Ormandy then developed a privilege escalation exploit which he shared with the mailing list, noting that another exploit was already in circulation.
The H's associates at heise Security were able to use the exploit to reproduce the problem. If the file is opened, it launches a command line which can be used to run arbitrary commands with system privileges, irrespective of the user's own privileges – even a guest account can be used.
Microsoft is likely to be less than happy at the security expert's decision to post an exploit online without contacting the company first. Microsoft publicly rebuked Ormandy following a similar incident three years ago. By employing a policy of full disclosure, he has forced Microsoft to act. The company will now have to plug the vulnerability as rapidly as possible, particularly given that black hats also now have access to the exploit code. A virus could utilise the exploit to shut down anti-virus software without a UAC prompt or to insert a rootkit deep into the system.
Microsoft told heise Security that it was looking into the problem and would "take appropriate measures" to protect its customers. It was not able to say when the vulnerability would be closed or how users could protect themselves from privilege escalation.
Ormandy's employer Google advocates responsible disclosure. This involves researchers who discover a vulnerability usually giving the manufacturer of the vulnerable software a grace period of 60 days prior to revealing details of their discovery. Where there is imminent danger because the vulnerability is already being actively exploited by hackers, Google has reduced this grace period to one week.
(fab)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








