Getting a grip on Flash cookies: Adobe publishes Flash 10.3
 Adobe has published version 10.3 of its Flash Player for all platforms. This version finally gives users control of their Flash cookies, but only if one of the currently supported web browsers is used: Firefox 4, Chrome 11, Internet Explorer 8 (or higher) and, soon, Safari. The new ClearSiteData API allows the browser to take care of Flash cookies (LSOs – Local Shared Objects), which it can manage as though they were normal cookies. Up until this release, users had to visit the Settings Manager on Adobe's website to handle the stubborn Flash cookies.
Adobe has published version 10.3 of its Flash Player for all platforms. This version finally gives users control of their Flash cookies, but only if one of the currently supported web browsers is used: Firefox 4, Chrome 11, Internet Explorer 8 (or higher) and, soon, Safari. The new ClearSiteData API allows the browser to take care of Flash cookies (LSOs – Local Shared Objects), which it can manage as though they were normal cookies. Up until this release, users had to visit the Settings Manager on Adobe's website to handle the stubborn Flash cookies.
Under Windows, Flash cookies can also be managed via a new entry in the control panel. Here, users will also find all of the settings that concern security and privacy. Flash 10.3 now also alerts Mac OS X users about updates automatically. Developers of VoIP applications can now access echo and noise suppression. Adobe has integrated the Media Measurement analysis function that provides developers with detailed usage statistics in combination with SiteCatalyst. The update for Flash Player Incubator, Adobe's test bed for new functions, will be of interest for developers with its JSON support and secure random number generator.
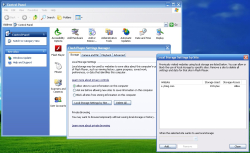
![]() Flash 10.3 allows users to decide the fate of Flash cookies via their control panel.
The update closes 11 security holes, most of which are critical memory flaws that allow attackers to inject malicious code. Adobe says that criminals are already actively exploiting one of the holes. The attackers send Word and Excel documents via email that contain infected Flash files. Adobe therefore strongly recommends that all users install the latest release, version 10.3.181.14, as soon as possible. Chrome users automatically get the new Flash Player plug-in version by updating to Chrome 11.0.696.68. Adobe has also patched vulnerabilities in Flash for Android in version 10.3.185.21.
Flash 10.3 allows users to decide the fate of Flash cookies via their control panel.
The update closes 11 security holes, most of which are critical memory flaws that allow attackers to inject malicious code. Adobe says that criminals are already actively exploiting one of the holes. The attackers send Word and Excel documents via email that contain infected Flash files. Adobe therefore strongly recommends that all users install the latest release, version 10.3.181.14, as soon as possible. Chrome users automatically get the new Flash Player plug-in version by updating to Chrome 11.0.696.68. Adobe has also patched vulnerabilities in Flash for Android in version 10.3.185.21.
Increasingly, rumors are circulating that a flaw in Flash is part of the reason for the recent breakout from the Chrome sandbox. Adobe did not, however, comment on whether a Flash hole was exploited during the breakout and, if so, whether the vulnerability was fixed with this update.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








