German researchers develop network scan for Conficker worm
Felix Leder and Tillmann Werner from the University of Bonn have analysed the Conficker worm and discovered that it changes the way Windows responds to certain system calls. This can be exploited to allow the remote detection of Conficker infected systems.
Specifically, a scanner can call the NetpwPathCanonicalize() function – which contains the vulnerability through which Conficker spreads – remotely. When present Conficker intercepts and deals with these calls and the response to this call is, in certain cases, modified. For the test to succeed on a Windows system, TCP port 445 must be accessible. This port is not normally (and indeed shouldn't be) accessible from the web.
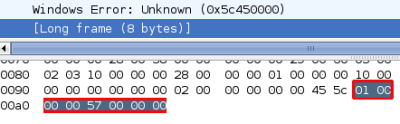
![]() The worm reveals itself by its response to the NetpwPathCanonicalize function.
The worm reveals itself by its response to the NetpwPathCanonicalize function.
Leder and Werner have written such a scanner as a feasibility demonstration. In collaboration with Dan Kaminsky, they have forwarded this information to the Conficker Working Group and other security experts, so that third party scanners offering this functionality are likely to be available soon, with Kaminsky announcing extensions for nmap, Tenable (Nessus), McAfee/Foundstone, ncircle and Qualys.
Company administrators are well advised to scan their networks for infected systems before 1st April – the date on which Conficker.C will begin to download updates from the internet. What the effect of these updates will be remains completely unknown. Many anti-virus software vendors are offering specific programs for removing Conficker. However, the safest option on an infected system is to reinstall the operating system and then copy over your backup data.
On the research project, see also:
- Detecting Conficker, announcement from the Honeynet Project.
- Scanner download, a ZIP file.
On the Conficker-Worm see also:
- Conficker worm reloads - maybe, a report from The H.
- Conficker infects UK parliament, a report from The H.
- Conficker to disrupt legitimate domains in March, a report from The H.
- Conficker becomes a more flexible worm, a report from The H.
- Microsoft, ICANN and others, move to block Conficker, a report from The H.
- F-Secure now claims nine million Conficker infections, a report from The H.
- Report: 2.5 million PCs infected with Conficker worm, a report from The H.
- Conficker in Carinthia: first the state government, now the hospitals, a report from The H.
- Windows worm infection accelerates, a report from The H.
(trk)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








