Front company used to sign malware
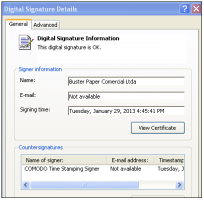
![]() The malware's valid signature displayed
The malware's valid signature displayed
Source: Malwarebytes
Using a shell company, criminals in Brazil purchased valid certificates from a certificate authority in order to sign malware, according to a report from Malwarebytes. The new method of obtaining signatures was detected when the criminals signed a banking trojan and other malware and put them into circulation.
The certificates were issues to a company called "Buster Paper Comercial Ltda" which apparently only existed on paper. The company was used to request a certificate from CA Digicert. Digicert told CIO Magazine that it did issue the certificate because at the time "Buster Paper Comercial Ltda was a legally registered business as confirmed through the Brazilian Ministerio da Fazenda: Cadastro Sincronizado Nacional." The certificate has since been revoked.
The trojan that was signed with the fraudulently obtained certificate was sent by email as an attached executable file. The executable was disguised as a PDF file which, once opened, installed malicious code, deployed further payloads and tapped the system to obtain bank account details and passwords.
Digitally signing malware has been used to give the user a false sense of security in the software and to get it past some defences in operating systems, but in the past, most of the certificates used have been stolen rather than applied for.
(djwm)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








