Flashback numbers not going down - still over half a million
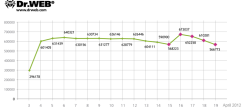
![]() Dr Web's estimate of Flashback infections
Dr Web's estimate of Flashback infections
Source: Dr Web
Initial reports of drops in the number of systems infected with the Flashback Mac malware are being corrected – the adjusted number is now back to around 550,000 systems. The corrections come after it was shown by Dr Web that one system among the various command and control IP addresses was halting bot scans. Flashback-infected machines randomly work through a generated range of different systems, connecting to each to check for commands. The blocking system meant that companies, like Dr Web, who set up their sinkhole servers earlier, so that they could estimate the number of infections, got to see more infected machines connecting, while sinkholes set up later saw fewer infected systems.
Connecting to the IP address Dr Web identifies does confirm the reported behaviour: the system accepts the connection but doesn't respond, leaving the TCP/IP connection open. Geolocation searches on the IP address show the system is apparently located in Fremont, California. It is unclear who operates the blocking system or what their purpose is.
Symantec updated its earlier blog posting in which it estimated 140,000 infected systems, noting a rise to 185,000 infected systems in its monitoring and concurring with Dr Web's reporting of a blocking sinkhole.The lack of a drop in numbers of infections is despite Apple first updating Java to close the hole, then updating again with a removal tool and offering a standalone removal tool. Some theorise that the numbers may reflect systems running Mac OS X 10.5 and earlier for which there have been no updates from Apple.
A recent analysis of Flashback by Kaspersky traces the initial distribution of the malware to WordPress blogs. It theorises that bloggers with vulnerable versions of WordPress or who had installed ToolsPack plugin were used to provide a platform for launching the malware on behalf of an apparently Russian cybercriminal partner programme. The WordPress blogs included scripts loaded from sites on .rr.ru domains. An estimated 30,000 to 100,000 blogs were compromised, with 85% of the blogs being in the US.
Meanwhile, Intego is reporting yet another Flashback variant that is says is in the wild. Dubbing it Flashback.S, Intego reports that it uses some new locations to place its files (~/Library/LaunchAgents/com.java.update.plist and ~/.jupdate) and actively cleans itself from the Java cache to avoid detection. The variant does not appear to use any new exploits but can still install itself in the user's account without a password being requested.
(djwm)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








