Flashback malware uses new infection technique
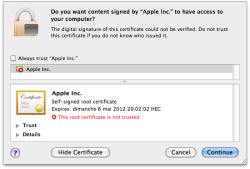
![]() The certificate used to tempt users to install the malware
The certificate used to tempt users to install the malware
Source: Intego
A new variant of Mac malware Flashback is using a new installation method. When a user visits a crafted web page, the new variant either tries to exploit two old security vulnerabilities or deploys a Java Applet which tries to trick the user into believing it has been certified by Apple – that's according to a blog posting from anti-virus company Intego. If the target system is running an outdated version of Java for Mac OS X, the malware is able to install itself directly without user intervention. If an up-to-date version of Java is in use, to become infected the user has to approve a certificate clearly marked as not trusted. Apple last updated Java for Snow Leopard and Lion in November 2011.
The malware, designated Flashback.G, apparently refrains from installing itself on systems which are running specific anti-virus products – according to Intego this is to avoid detection. Most of the infections observed by Intego have been on systems running Mac OS X 10.6. Java is not installed by default on 10.7 Lion, but must be installed manually by the user. Snow Leopard users should therefore check the Software Update application for any outstanding Java updates.
Flashback has in the past disguised itself as a Flash installer. Following successful installation, it apparently attempts to steal user names and passwords entered in browsers and other applications which access the web and forwards them to the malware controller.
(djwm)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








