Exploit on Amnesty pages tricks AV software
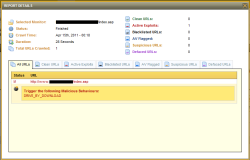
![]() Many behaviour recognition routines can now detect drive-by downloads
Many behaviour recognition routines can now detect drive-by downloads
Source: Armorize
On its blog, security firm Armorize has reported on a clever exploit on certain web sites that infected visitors' computers with malware. Apparently, criminals injected a "drive-by download" on web sites such as that of human rights organisation Amnesty International.
Armorize says that the exploit took advantage of a security hole in Flash that was only fixed via an emergency patch by Adobe a few days ago. What made the attack special was the way in which the criminals exploited the hole. The security hole allowed them to inject arbitrary code and execute it in Flash Player. Typically, such "shell code" will use the URLDownloadToFile() function to retrieve the actual spyware from another server and then execute it. Since this function is only rarely used by browsers themselves, the heuristics or behaviour recognition features of modern anti-virus programs tend to become suspicious when they detect such activities and can, if necessary, even intervene to prevent an infection.
The criminals used a trick to avoid this. Using a script tag, they embedded the spyware in a web site as a file purporting to contain JavaScript. Consequently, users' browsers downloaded the file, stored it in cache and then tried to execute it. Execution failed because the file actually contained an executable Win32 program instead of JavaScript code – but that didn't matter. Now, the shell code started via Flash could simply, and without the need for further downloads, search for the file in the browser cache on the user's hard disk and execute from there.
Armorize says that the trick was resoundingly successful. Although the Flash hole is a known vulnerability, not a single one out of 42 virus scanners reportedly exposed the malicious Flash file as a security risk. The posting on the Armorize blog offers further details, but it also contains exploit code that may trigger a virus monitor alarm.
(ehe)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








