EMET 4.0 catches SSL spies

![]() The new configuration wizard means users don't have to be security experts to activate key protection features
The new configuration wizard means users don't have to be security experts to activate key protection features
Microsoft has taught version 4.0 of the Windows mitigation tool EMET some new tricks. It now detects attacks that attempt to eavesdrop on encrypted connections and is better at thwarting return-oriented programming (ROP) attacks. The biggest change, however, is more cosmetic – EMET 4.0's revamped user interface makes it much easier to use. As a result, the handy mitigation tool should appear less intimidating to less technically-minded users.
After installation, the tool displays a configuration wizard, which can be used to set key security settings with just a few mouse clicks. This basic configuration includes protection profiles for popular programs such as Java, Adobe Reader and Office. This activates various exploit-blocking features, which are able to prevent many cyber-attacks even where these attacks target unpatched vulnerabilities. The new version also offers better protection from ROP exploits.
EMET 4.0 can also activate SSL Certificate Pinning for Internet Explorer. This involves setting up a whitelist specifying which certificate authorities (CAs) are permitted to issue SSL certificates for specific domains. If, on accessing a domain, a certificate from another CA is supplied, the mitigation tool displays a warning – even if the certificate is from a CA that Windows normally trusts.
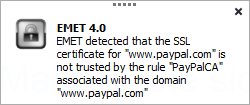
Genuine certificate, fake CA. The CA which issued this SSL certificate for paypal.com is not on the whitelist
It is very rare for major web services such as PayPal, Google and Twitter to change the CA for their SSL certificates. If, on visiting google.com, a certificate, not from GeoTrust or VeriSign, but from some other more obscure CA is delivered, there's a good chance that foul play is involved. In the past, fake SSL certificates have often been used for government surveillance.
Google's Chrome browser has long supported certificate pinning, though in Chrome the whitelist is hard-coded. It has already successfully detected some improperly issued google.com certificates.
There is also a new Early Warning feature, though the benefit it offers is indirect. If activated, EMET sends telemetry data on blocked attacks to Microsoft, providing the company with early warning of any zero days or SSL man-in-the-middle attacks. Last but not least, Microsoft reports that its developers have fixed all known compatibility problems and updated EMET so that it now works with Internet Explorer 10 and Windows 8.
(fab)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








