DNS provider's error caused LinkedIn "hack" and affected 5,000 more
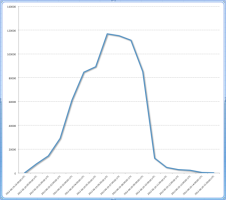
![]() The traffic redirection effect can be seen in this graph.
The traffic redirection effect can be seen in this graph.
Source: Cisco
LinkedIn, the professional networking site which had been reported as hacked or hijacked yesterday, was in fact the victim of human error at the company's DNS provider, Network Solutions, an error which appears to have affected up to 5,000 domains in all. Network Solutions has said in a blog posting that while trying to resolve a DDoS (Distributed Denial of Service) attack, it accidentally changed the DNS records of a "small number" of customers.
According to Cisco security researcher, Jaeson Schultz, the 'hijacking' involved the domain's name servers being replaced with name servers at ztomy.com and nearly 5,000 domains may have been affected by the change, including usps.com. Others affected included Fidelity and Yelp. Curiously, several of the domains pointed not at ztomy.com itself but to various sub-domains such as ns1620.ztomy.com, ns2620.ztomy.com, ns1621.ztomy.com, ns2621.ztomy.com and so on. "The fact that so many domains were displaced in such a highly visible way supports Network Solutions’ claim that this was indeed a configuration error", says Schultz
The ztomy.com name servers were configured to reply with addresses in the 204.11.56.0/24 range.That range is the IP range of a service provider, Confluence Networks. Given that DNS hijackings can enable the stealing of session cookies or users being guided to malware or phishing pages, suspicions that the redirection was malicious were high. Upon observing the incoming traffic, Confluence Networks put information about the problem on its web page, saying it had got in touch with affected parties to try and identify the source of the problem.
Meanwhile, the Cisco researcher recommends that anyone with a Network Solutions registered domain should check that their name servers are pointed at the right servers and suggests that administrators check logs for connections to the 204.11.56.0/24 subnet. Schultz closes, saying, "Organizations need to carefully consider how they would swiftly identify unauthorized modifications to their DNS records and how they would react to such a situation."
(djwm)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








