Cult of the Dead Cow turns Google into a vulnerability scanner
The "Cult of the Dead Cow" hacker group – cDc for short – has published a tool that searches for vulnerabilities and private information across the web. Using well-chosen Google search queries, Goolag Scan discovers links to vulnerable web applications, back doors, or documents inadvertently put on the internet that contain sensitive information.
This kind of "Google hacking" is already well known: a hacker using the pseudonym Johnny has already published quite a collection of these "Google Hacks" or "Google Dorks" on his web site ihackstuff. What cDc has done is create an automated tool that allows an unskilled hacker to use these same techniques.
When cDc created a furore ten years ago by publishing the back-door program Back Orifice it was also not a total innovation: back door programs giving hackers remote control of computers via a network had existed for some time. The publication of Back Orifice was nevertheless a milestone: it demonstrated how easy it is to take complete remote control of a PC running Windows.
Goolag Scan is cDc's latest attempt to rub salt into the wound. "Private individuals, firms, and even governments are putting more and more stuff on the web, and nobody cares what it means for security", explained cDc member Oxblood Ruffin to heise Security. cDc says it is publishing this tool now to let everyone check their own web site for vulnerabilities, and do something about them.
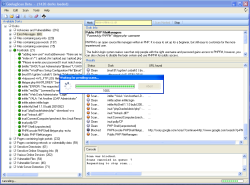
Goolag Scan is a small .NET program that provides around 1,500 pre-configured Google search queries in categories such as "vulnerable servers", "sensitive online shopping information" and "files containing juicy information". You can select individual searches or sets of them, then get Google to look for matching results. You can restrict the search to your own server, or extend it right up to an entire top-level domain, e.g. ".uk". Caution is advised: use the tool too much and there's a chance Google will become suspicious and block your IP address.
Goolag Scan presents the result as a list of URLs that can be opened directly in the browser. This frequently reveals access data, tell-tale error messages, or Java applets for the remote control of surveillance cameras.
The legality of such a tool appears to vary across Europe. In the UK, the situation is unclear at present. Using the links returned by Goolag Scan to gain access to a third party's content might be an offence or not, depending on several factors. If the owner of the material had intended that the content should be private, it would be necessary to obtain authorisation to access it in order to stay within the law, regardless of how it could be accessed. There is no requirement in CMA that protection must be circumvented for access to be unlawful, so contributory negligence on the part of the content owner in failing to protect content intended to be private would probably be irrelevant. However, the law in question (the Computer Misuse Act 1990 as amended by the Police and Justice Act 2006 – CMA) has not yet been tested, so there is no precedent and therefore no certainty.
It is also uncertain whether the act of obtaining the URLs using Goolag Scan would be lawful. The CMA now makes it unlawful to "enable (unauthorised) access to be secured", so obtaining a URL pointing to a private resource could of itself be an offence , even if that URL were publicly accessible. However, the question has not so far come before the Courts.
Despite Germany's anti-hacking legislation being in some respects the most stringent in Europe, heise Security believes Goolag Scan users there are unlikely to fall foul of the law because the data it reveals are publicly accessible. German data protection laws, particularly the new anti-hacker law passed last year, would only apply if the program was used as part of a planned or actual criminal act. So running Goolag Scan out of curiosity, and not using its findings for criminal acts, probably does not constitute an offence. However, this has not been tested yet in the Courts, so caution is again recommended.
Due to such concerns, despite an assurance by Oxblood that "We are releasing gS to enable everyone - whether they're private users, enterprise, or government - to audit their own Web sites and see if their pants are hanging down. And if they are, then they can correct these problems", heise online feels unable to test Goolag Scan for ourselves, or indeed advocate its use within the jurisdiction of English law.
(mba)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








