Cracking attack on Twitter
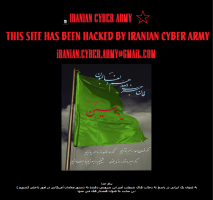
![]() Instead of tweets, users accessing the home page of the Twitter micro-blogging service on Friday morning were presented with an "Iranian Cyber Army" page. The actual originator of the attack, however, remains unknown.
Instead of tweets, users accessing the home page of the Twitter micro-blogging service on Friday morning were presented with an "Iranian Cyber Army" page. The actual originator of the attack, however, remains unknown.
According to a post on the Twitter blog, the crackers manipulated DNS entries in such a way that users trying to access Twitter.com reached a server controlled by the crackers instead of the Twitter pages. Reportedly, Twitter's own servers were not attacked. The DNS entries have since been corrected, and Twitter.com is accessible again. Users running third-party desktop or mobile clients which use the Twitter API didn't encounter the problem.
Twitter doesn't mention how the crackers carried out the DNS manipulation. It could be that a Twitter admin fell victim to a phishing attack and disclosed the access credentials for configuring the DNS data at the registrar. In the past week, several security firms registered an increased number of such attacks on administrators. A similar wave of phishing attacks to obtain registrar access data occurred last year. At the time, ICANN responded by issuing a warning.
See also:
- Shutting Twitter backdoors, a report from The H.
- Twitter fails to block Cross Site Scripting flaw, a report from The H.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








