Bootkit bypasses hard disk encryption
At the Black Hat security conference, Austrian IT security specialist Peter Kleissner presented a bootkit called Stoned which is capable of bypassing the TrueCrypt partition and system encryption. A bootkit combines a rootkit with the ability to modify a PC's Master Boot Record, enabling the malware to be activated even before the operating system is started.
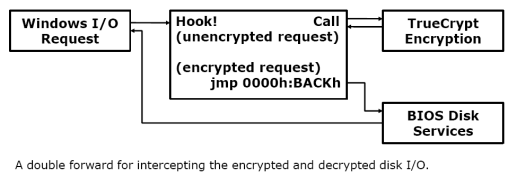
Available as source code, Kleissner's bootkit can infect any currently available 32-bit variety of Windows from Windows 2000 to Windows Vista and the Windows 7 release candidate. Stoned injects itself into the Master Boot Record (MBR), a record which remains unencrypted even if the hard disk itself is fully encrypted. During startup, the BIOS first calls the bootkit, which in turn starts the TrueCrypt boot loader. Kleissner says that he neither modified any hooks, nor the boot loader, itself to bypass the TrueCrypt encryption mechanism. The bootkit rather uses a "double forward" to redirect I/O interrupt 13h, which allows it to insert itself between the Windows calls and TrueCrypt. Kleissner tailored the bootkit for TrueCrypt using the freely available TrueCrypt source code.
Once the operating system has been loaded, Stoned can get to work and install malware, such as a banking trojan, in the system. Peter Kleissner, who is only 18 years old, has also included several plug-ins, for example a boot password cracker and a routine for infecting the BIOS. The framework layout of Stoned allows other programmers to develop their own plug-ins for the bootkit. Kleissner thinks that Stoned could also be of interest to investigation agencies, for example for developing a federal trojan.
Once installed, Stoned cannot be detected with traditional anti-virus software because no modifications of Windows components take place in memory, says Kleissner. Stoned runs in parallel with the actual Windows kernel. Even an anti-virus function in the BIOS can't stop the bootkit, as modern Windows versions modify the MBR without referring to the BIOS.
However, administrator privileges or physical access to a system are required for an infection. At present, only machines running the traditional BIOS are vulnerable. The attack is unsuccessful when the BIOS successor the Extensible Firmware Interface (EFI) is at work on the motherboard. The most effective protection appears to be encrypting the entire hard disk with software that is based on the Trusted Platform Module (TPM).
For instance, using Windows' own BitLocker encryption mechanism is said to be a reliable antidote, because an infected MBR's hash value no longer corresponds to the hash value stored in the TPM, prompting the TPM to abort the boot process. Kleissner didn't have an answer to the question whether a hardware-encrypted hard disk is capable of preventing an infection.
(Uli Ries)
(djwm)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








