Attacks on German mTAN banking users
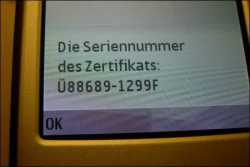
![]() An innocuous message is displayed after installation on a mobile.
An innocuous message is displayed after installation on a mobile.
Source: F-Secure
Anti-virus software vendor F-Secure is reporting that a new version of internet banking trojan SpyEye uses sophisticated methods to intercept mTANs sent to mobile phones. In contrast to big brother Zeus, SpyEye appears to have its sights set on German internet banking users.
The mTAN procedure, introduced by many German banks to replace (i)TANs, which were considered insecure, involves the bank sending a text containing the TAN and transaction data to a previously saved mobile phone number. An online banking trojan which has infected a Windows system is left with no opportunity to interfere with this data – or at least not directly.
Consequently, Zeus and SpyEye have learned to deploy a new trick. They insert a message on the online banking web page stating that a new certificate for the bank needs to be uploaded to the user's mobile phone. The user is asked to enter their mobile phone number and IMEI. A little later, they receive a message containing what purports to be an installer for the new certificate. If they launch the installer, the following message (in German) is displayed: "Die Seriennummer des Zertifikats: 88689-1299F" (The serial number of the certificate: 88689-1299F).
While this is happening, the trojan is installing spyware on the phone in the background. Analysis of its functionality is still ongoing, but it appears to forward incoming mTAN details to a web server via the internet. The spyware is designed for Symbian smartphones, such as those produced by Nokia. For software to be installed on a Symbian mobile without popping up anything too eye-watering by way of warning messages, it needs to be digitally signed. To get around this, the SpyEye trojan is signed using a developer certificate of the type which can be obtained free of charge from Chinese service provider OPDA. These certificates have to contain the target mobile's IMEI, which is why the trojan requests this information, which it then uses to generate a specially tailored version.
The attack raises serious questions about the security of the mTAN procedure. The usual advice to only install apps from trusted sources is no longer adequate. Since the app in this case appears to have been sent by the bank, many users are likely to fall for this trick and they cannot be accused of having exercised inadequate care. It is therefore high time that banks using mTANs explain how they intend to protect their customers in future.
See also:
- Online banking trojan developing fast, a report from The H.
- Spy versus spy: Tracker for SpyEye control servers launched, a report from The H.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








