Attackers set sights on online industrial control systems
 The US government's Industrial Control System Cyber Emergency Response Team (ICS-CERT) is warning
The US government's Industrial Control System Cyber Emergency Response Team (ICS-CERT) is warning![]() that searches for SCADA systems accessible via the web are increasing. SCADA (Supervisory Control and Data Acquisition) systems are used to monitor and configure industrial control systems for devices such as pumps and motors. Attackers can attempt to penetrate and manipulate such systems via known default passwords or security vulnerabilities. By changing target parameters, attackers may be able to cause faults or failures, depending on the application.
that searches for SCADA systems accessible via the web are increasing. SCADA (Supervisory Control and Data Acquisition) systems are used to monitor and configure industrial control systems for devices such as pumps and motors. Attackers can attempt to penetrate and manipulate such systems via known default passwords or security vulnerabilities. By changing target parameters, attackers may be able to cause faults or failures, depending on the application.
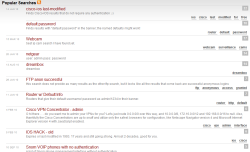
![]() Cisco systems, webcams and VoIP phones are among the most popular searches.
ICS-CERT's assessment appears to be based on the search terms being entered into the specialist search engine SHODAN in order to discover vulnerable systems. SHODAN assesses global web, FTP, SNMP, SSH and Telnet server banners, which contain information on the product, version and a range of further data. To find an OpenSSH server running the ancient version 3.7, for example, a user merely needs to enter 'openssh 3.7' into the search engine to receive a list of servers likely to be vulnerable. The search can be refined, including restricting it to a specific country. There is nothing new about searching for SCADA systems on the web, but SHODAN makes the whole process much easier.
Cisco systems, webcams and VoIP phones are among the most popular searches.
ICS-CERT's assessment appears to be based on the search terms being entered into the specialist search engine SHODAN in order to discover vulnerable systems. SHODAN assesses global web, FTP, SNMP, SSH and Telnet server banners, which contain information on the product, version and a range of further data. To find an OpenSSH server running the ancient version 3.7, for example, a user merely needs to enter 'openssh 3.7' into the search engine to receive a list of servers likely to be vulnerable. The search can be refined, including restricting it to a specific country. There is nothing new about searching for SCADA systems on the web, but SHODAN makes the whole process much easier.
According to ICS-CERT, attackers have used SHODAN to discover and target individual PCs and central systems accessible via dedicated WANs. The organisation reports that it is working with vendors and service providers to inform users operating vulnerable systems of the problem. The ICS-CERT warning recommends making all SCADA systems accessible via VPN only, deleting default accounts from systems and using more secure passwords.
In recent weeks, since the Stuxnet attacks, there has been a flood of reports on the security or lack of it of critical infrastructure in which SCADA and ICS systems are deployed. The issue is actually somewhat old hat, but is an issue that, until now, only specialists have taken note – and long warned of the dangers. Until Stuxnet came along they were widely ignored. From this point of view, Stuxnet may have done some good. Like Blaster and SQL Slammer once was for Windows, Stuxnet has been a wake-up call for SCADA security.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








