American Express fixes critical security vulnerability

Charge card company American Express has fixed a security vulnerability on its web site that allowed SQL injection and, therefore, direct access to its server's database. The company acted after The H's associates at heise Security![]() forwarded a tip-off from one of its readers.
forwarded a tip-off from one of its readers.
Student Nils Kenneweg had discovered that the pages of the American Express web site did not adequately filter data passed to a search function, thereby allowing direct access to the database server. He sent a message about this SQL injection problem to the heise Security team, who were able to reproduce it; the information was then passed on to American Express.
The company reacted quickly and fixed the vulnerability within a few days. It stated that the vulnerability had not been used and no customer data had been compromised. Some doubt exists about this statement, however, since SQL injection frequently allows access to all of an affected system's data, and tables with names like "Accounts" often show up in SQL statements.
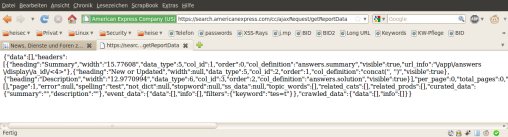
![]() Cleverly designed queries could have been used to communicate directly with the server's SQL database
Cleverly designed queries could have been used to communicate directly with the server's SQL database
Of particular concern is that the vulnerability was found not in some hidden corner but in the search function – the first place someone would test for such problems. A web site that is regularly tested and systematically secured should not have this kind of vulnerability in such an exposed location.
(ehe)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








