Adobe aims to get Reader out of the firing line
 Adobe has reacted to the continuing attacks on Adobe Reader. The next version – which will likely be called Adobe Reader 10 – will include a sandbox which will, according to Brad Arkin, responsible for security of all Adobe software products, make Reader a less attractive target for attackers. However, Arkin did not want to commit to a date for releasing the new technology, officially dubbed Adobe Reader "Protected Mode".
Adobe has reacted to the continuing attacks on Adobe Reader. The next version – which will likely be called Adobe Reader 10 – will include a sandbox which will, according to Brad Arkin, responsible for security of all Adobe software products, make Reader a less attractive target for attackers. However, Arkin did not want to commit to a date for releasing the new technology, officially dubbed Adobe Reader "Protected Mode".
The most important function of the sandbox, which will be activated by default, is to block write access to Windows systems from Adobe Reader. Until now, having taken control of Reader (by exploiting buffer overflows or embedded JavaScript for example) attackers have been able to mess around in the system with the privileges enjoyed by Reader. The sandbox puts an end to this and prevents changes being made to the registry or files on the hard drive, prevents processes from being launched and blocks access to named pipes or named shared memory. All PDF functions, such as displaying images, 3D effects, execution of JavaScript or multimedia content, take place within the sandbox. PDFs opened using browser plug-ins will also run in the Reader process irrespective of browser security settings.
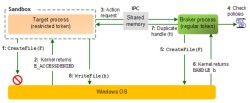
![]() The broker process uses fixed rules to decide when access to the system from Adobe Reader should be blocked.
Technically, Adobe's sandbox is based on a Microsoft technology known as Microsoft Office Isolated Conversion Environment (MOICE) which is already in use in Office 2010. A broker process processes all write queries from the sandbox and decides whether or not they are legitimate based on a defined set of rules. Adobe states that the broker process and sandbox code has been kept very lean and has been tested by external penetration testers. Arkin has confirmed that Adobe is also considering using the sandbox to trap read access and thus block access to sensitive data on the system.
The broker process uses fixed rules to decide when access to the system from Adobe Reader should be blocked.
Technically, Adobe's sandbox is based on a Microsoft technology known as Microsoft Office Isolated Conversion Environment (MOICE) which is already in use in Office 2010. A broker process processes all write queries from the sandbox and decides whether or not they are legitimate based on a defined set of rules. Adobe states that the broker process and sandbox code has been kept very lean and has been tested by external penetration testers. Arkin has confirmed that Adobe is also considering using the sandbox to trap read access and thus block access to sensitive data on the system.
Adobe does not see the sandbox as a panacea. It will not, for example, block phishing, clickjacking, weak encryption in signed documents or unauthorised network access. There may also be issues for users using assistive technologies such as screen readers under Windows XP and Windows Server 2003.
The vendor is promising the ability to disable protected mode or to use registry entries to add new rules in the event of problems. Company administrators will be able to implement these easily using group policies.
(Uli Ries)
(Uli Ries / crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








