ASLR on Android 4 found wanting
 Jon Oberheid has found the ASLR (Address Space Layout Randomisation) in Google's Android 4, Ice Cream Sandwich (ICS), somewhat wanting. In a detailed posting on the Duo Security blog, one commenter eloquently concluded that "TL;DR: ICS ASLR = FUBAR".
Jon Oberheid has found the ASLR (Address Space Layout Randomisation) in Google's Android 4, Ice Cream Sandwich (ICS), somewhat wanting. In a detailed posting on the Duo Security blog, one commenter eloquently concluded that "TL;DR: ICS ASLR = FUBAR".
Specifically, he found that the lack of randomisation in executable and linker memory regions meant that it would be "largely ineffective for mitigating real-world attacks". Oberheid shows that Android inherits ASLR from Linux, but prior to ICS it was "almost non-existent" with only the location of the stack being randomised.
In ICS 4.0, with its Linux 3.x kernel, it was believed that Linux's ARM ASLR additions would function. But on examination, it is only a slight improvement with libc.so and other shared libraries randomised, but not the heap, executable code or linker mappings.
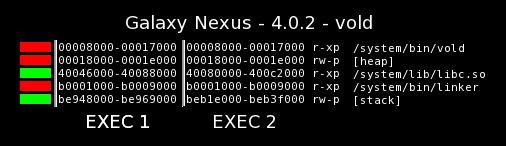
![]() Many important code ranges are still at the same address
Many important code ranges are still at the same address
Source: Duo Security
Oberheid looks into the reasons and mitigations for each of these and also notes other concerns about ASLR in connection with the zygote process launching system. The Android Security Team responded to Oberheid's posting noting that they will, in 4.0.3, randomise the heap and future Android releases will randomise the linker and executable mappings.
(djwm)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








