Identity theft with OpenID
 The OpenID Foundation has warned that flawed implementations of the Attribute Exchange (AX) OpenID extension allow potential attackers to assume other users' identities on certain web sites. Security researchers had found that some web sites which participate in OpenID don't verify whether the transmitted data has been signed. This insufficient verification reportedly allows attackers to arbitrarily manipulate the data. The Foundation didn't suggest a specific attack scenario.
The OpenID Foundation has warned that flawed implementations of the Attribute Exchange (AX) OpenID extension allow potential attackers to assume other users' identities on certain web sites. Security researchers had found that some web sites which participate in OpenID don't verify whether the transmitted data has been signed. This insufficient verification reportedly allows attackers to arbitrarily manipulate the data. The Foundation didn't suggest a specific attack scenario.
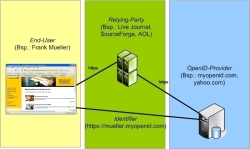
![]() Roles, terms and examples in the OpenID environment.
The Foundation didn't state which web sites were affected by the problem. The operators of the vulnerable sites were reportedly informed of the vulnerability in advance and have apparently all closed the hole. According to the Foundation, the problem mainly affects applications which use the OpenID4Java Java library.
Roles, terms and examples in the OpenID environment.
The Foundation didn't state which web sites were affected by the problem. The operators of the vulnerable sites were reportedly informed of the vulnerability in advance and have apparently all closed the hole. According to the Foundation, the problem mainly affects applications which use the OpenID4Java Java library.
The vulnerability was closed in the final version 0.9.6 of the library. The Kay framework for Google's App Engine is also vulnerable up to version 1.0.1, which has now been superseded – the current version is 1.1.1. The Foundation said that, while other libraries could potentially also be affected, Janrain, Ping Identity and DotNetOpenAuth are probably not vulnerable.
OpenID is an attempt to establish an open source single sign-on system on the net. Users who register with an OpenID provider such as Google, Yahoo, WordPress or MySpace can use their access data to sign into any of the participating internet services.
(crve)
![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)
















