Google protects connections with forward secrecy

Google has announced that it has enabled forward secrecy in its HTTPS services by default. Most HTTPS sites operate in such a way that a private key is retained and, theoretically, that key could be broken in the future, giving someone the ability to decrypt all the traffic that was encrypted with that key. Forward secrecy ensures that captured messages cannot be decrypted en masse by making sure that the private keys used to encrypt connections are not kept on persistent storage. "Not even the server operator will be able to retroactively decrypt HTTPS sessions," says Google.
Forward secrecy is live on Gmail, SSL Search, Docs and Google+. To see whether it is operating, Google suggests that users click on the green padlock in a Chrome window and check that the key exchange mechanism is shown as ECDHE_RSA as shown below:
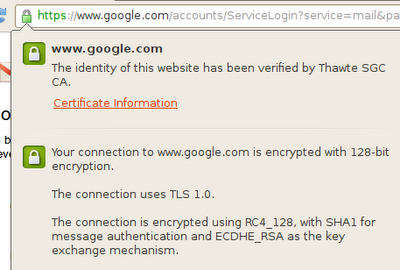
![]() Forward secrecy is enabled when ECHDE_RSA is shown as the key exchange mechanism
Forward secrecy is enabled when ECHDE_RSA is shown as the key exchange mechanism
Source: googleonlinesecurity.blogspot.com
Chrome, Firefox and Internet Explorer support Google's forward secrecy mechanism, but Internet Explorer does not enable it by default as it does not support the combination of ECHDE (Elliptic Curve Diffie-Hellman Exchange) and RC4 that Google is using. Google hopes to support IE in the future. Google has also released its modifications to the OpenSSL Library that allowed it to enable forward secrecy and which is due to appear in OpenSSL 1.0.1.
(lcz)
![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)
















