GitHub security incident highlights Ruby on Rails problem
![]() Egor Homakov's demonstration of Rails and GitHub vulnerabilities
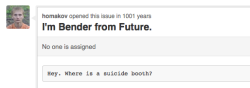
Egor Homakov's demonstration of Rails and GitHub vulnerabilities
On Sunday morning, 4 March, Egor Homakov exploited a flaw in how the Ruby on Rails web framework handles mass assignments that allowed him to write a posting, delete a posting or push changes into source code on any GitHub project. Homakov had previously created an issue regarding mass assignment security on the rails issue tracker on GitHub; this was closed by the developers saying that it was the application developers' responsibility to secure their applications. Homakov then decided to demonstrate the issue using the nearest Ruby on Rails application, GitHub.
He first created an issue on the Rails project's issues list timestamped 1001 years into the future, to get the attention of the Rails developers. Then, he added his public key to the list of Rails committers and made a commit to the Rails master repository. GitHub suspended Homakov's account, while they fixed the problem. After GitHub fixed the issue, Homakov published a how-to on how he had manipulated GitHub's Rails applications.
The problem, known as the mass assignment vulnerability, has been around since the ability to set a number of attributes in one call was introduced in Rails. The problem is listed in the Rails Security Guide, which also details how to blacklist or whitelist the attributes being set, but this functionality is not enabled by default so many Rails applications still have the issue. In GitHub's case, Homakov manipulated the PublicKey records and associated user ids to make a created SSH key appear to be the public key of a victim by modifying the results in the Public Key form page.
GitHub has said that it has initiated a full audit of its code which is ongoing. In a follow-up posting, the company said that Homakov had disclosed an issue to them two days previously, but then found the "public key form update vulnerability" and exploited it without disclosure. The company says "Now that we've had a chance to review his activity, and have determined that no malicious intent was present, @homakov's account has been reinstated". Github has also added a guide to their help pages explaining how to responsibly disclose security issues to them.
However, the mass assignment issue is still an issue for many other Rails applications and it is recommended that developers audit their code to ensure that they do not allow their systems to be manipulated in the same way. A recent commit to the Rails code will set the requirement to whitelist attributes on by default, but only for newly created applications; it is expected to be included in an update to Rails 3.2.
(djwm)
![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)
















