Firefox WebSocket bug compromises Tor anonymity
![]() Disabling WebSocket in Firefox
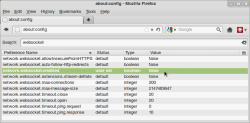
Disabling WebSocket in Firefox
The current versions of the Tor Browser Bundle (TBB) include a bug that makes it possible for information about visited web sites to leak out of the anonymising layer. On version 2.2.35-9 of TBB for Windows and version 2.2.35-10 for Mac OS X and Linux, the included version of Firefox does not send DNS requests over the Tor network if the browser is using the WebSocket protocol. This means that an attacker listening in on the connection will be able to identify the servers the user is visiting.
The only workaround for the problem currently is to completely disable the use of WebSocket in the browser. Users can do this by accessing Firefox's advanced configuration options by entering about:config in the address bar and changing the network.websocket.enabled option to "false".
The Tor developers are currently working on a fix for the security hole and will be releasing a new TBB version soon. More information on the issue can be found in the bug report on the Tor project's issue tracking system.
(fab)
![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)
















