ENISA promotes digital hacker traps
 The European Network and Information Security Agency (ENISA) recommends that honeypots be used to detect threats at an early stage; the agency tested 30 current systems and came up with concrete recommendations.
The European Network and Information Security Agency (ENISA) recommends that honeypots be used to detect threats at an early stage; the agency tested 30 current systems and came up with concrete recommendations.
Honeypots are digital traps used to analyse cyber attacks and their strategies and tools. In the study, ENISA tested honeypots for effectiveness and practicality, with a focus on open-source honeypots. The results are intended to help companies find the best digital traps for their particular situations and to promote further development in the area.

![]() The study points out recommended honeypots with smiley faces.
The study points out recommended honeypots with smiley faces.
Source: ENISA
The evaluation system developed for the ENISA study places particular emphasis on user-friendliness. ENISA employees used the honeypot evaluation procedure![]() developed in 2006 by Christian Seifert, Ian Welch and Peter Komisarczuk as a basis for the system and added more "practical" categories. They also differentiated more between various types of honeypots; types tested include server-side honeypots, client-side honeypots, low-interaction honeypots, high-interaction honeypots, hybrid honeypots and sandboxes. Open source online honeypots for monitoring suspicious URLs were also evaluated.
developed in 2006 by Christian Seifert, Ian Welch and Peter Komisarczuk as a basis for the system and added more "practical" categories. They also differentiated more between various types of honeypots; types tested include server-side honeypots, client-side honeypots, low-interaction honeypots, high-interaction honeypots, hybrid honeypots and sandboxes. Open source online honeypots for monitoring suspicious URLs were also evaluated.
As part of the study findings, ENISA recommends a number of digital traps, noting that dionaea, Glastopf, kippo and Honeyd are particularly easy to use. Among the client honeypots, Thug and Capture-HPC NG also received special mentions.
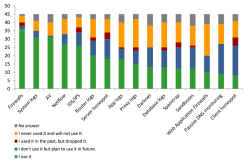
![]() Honeypots tend not to be a company's first choice for security monitoring.
Honeypots tend not to be a company's first choice for security monitoring.
Source: ENISA
ENISA sees room for improvement when it comes to honeypots' analysis tools. Although data on attacks is collected, it is not processed in a way that makes it easy to analyse. Some current open-source honeypot projects are so complicated that users need more specialist knowledge than for many other security solutions. That's most likely one of the main reasons that a majority of the security teams surveyed for the study prefer to use firewalls, log files and antivirus programs to gather information on network security issues.
Nevertheless, ENISA still advises companies to set up digital traps, as even the recommended programs are freely available and cost nothing. Some open source honeypots may need some more development, they say, but the more security teams decide to use digital traps, the more likely it is that honeypots would be constantly updated and would therefore be a solid solution for registering and quickly reacting to malicious activity. Professor Udo Helmbrecht, executive director of ENISA, adds that honeypots are powerful tools that CERTs (Computer Emergency Response Teams) can use to have "threat intelligence collected without any impact on production infrastructure".
The complete study titled Proactive Detection of Security Incidents![]() can be downloaded for free.
can be downloaded for free.
(djwm)
![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)
















