DOM flaw can crash many browsers
![]() The CrashThisThing proof of concept
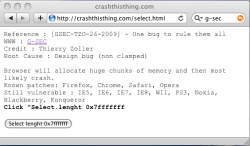
The Luxembourg security specialists G-SEC have published details of a vulnerability in the majority of browsers which will either crash the browser or consume so much memory that it makes the computer virtually unusable. The trick is simple. Using JavaScript's DOM (Document Object Model), create a selection menu on the web page; a select element. Then assign to that select element's length attribute a very high value, as a result there is a continuous allocation of memory. The length attribute specifies the number of menu items the select element should contain, and according to the specification (and common sense) should be read only, but in many cases, it is writeable.
The CrashThisThing proof of concept
The Luxembourg security specialists G-SEC have published details of a vulnerability in the majority of browsers which will either crash the browser or consume so much memory that it makes the computer virtually unusable. The trick is simple. Using JavaScript's DOM (Document Object Model), create a selection menu on the web page; a select element. Then assign to that select element's length attribute a very high value, as a result there is a continuous allocation of memory. The length attribute specifies the number of menu items the select element should contain, and according to the specification (and common sense) should be read only, but in many cases, it is writeable.
A proof-of-concept shows that not all browsers are affected by the problem. In a test on a Windows Vista system, only Internet Explorer 8 was affected and crashed. Firefox, Safari and Chrome seemed unaffected. Opera used a large amount of RAM but remained operational – according to G-SEC this problem is fixed in the forthcoming version.
G-SEC say that, Firefox 2.0.19 and 3.0.5 fix the problem, but earlier versions will use up all available memory and then crash, as will older versions of Chrome and Safari. On a system with Konquerer and Ubuntu, it was found that either the browser crashed or the system rebooted. The reboot is apparently caused by Ubuntu's memory management system killing a random process, rather than the memory hogging process.
According to Thierry Zoller of G-SEC, Opera undertook to fix the bug in version 9.64 but has apparently not done so. Microsoft wants to fix the problem in Internet Explorer 9, which will probably have a new JavaScript engine. Also affected are the browsers on most mobile devices (iPhone, Android and Symbian) and gaming consoles (Wii and PS3), though iPhone and Android devices with the current WebKit based browsers have corrected the problem.
Thierry Zoller points out that this is an old vulnerability, first found nine years ago in Netscape 6. As other browsers vendors sought to make their browsers compatible, the same mistake was made in all common browser engines before G-SEC brought it to their attention.
(djwm)
![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)
















