Android apps send unencrypted authentication token
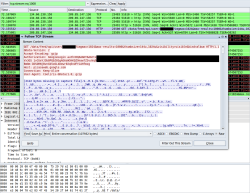
![]() The authentication token is transmitted when accessing Picasa via the API - however, on an unsecured Wi-Fi network, anyone can intercept and misuse the token.
Attackers can potentially exploit an Android data transmission vulnerability to gain access to, and manipulate, other users' Google Calendar, Picasa Web Album and Google Contact data. The issue exists because an authentication token (authToken) received when logging into the Google server is subsequently transmitted in plain text by some applications. Researchers at Ulm university in Germany report that, in unencrypted Wi-Fi networks and in networks where all users use the same Wi-Fi key, attackers can potentially use Wireshark to intercept the token and use it for their own purposes.
The authentication token is transmitted when accessing Picasa via the API - however, on an unsecured Wi-Fi network, anyone can intercept and misuse the token.
Attackers can potentially exploit an Android data transmission vulnerability to gain access to, and manipulate, other users' Google Calendar, Picasa Web Album and Google Contact data. The issue exists because an authentication token (authToken) received when logging into the Google server is subsequently transmitted in plain text by some applications. Researchers at Ulm university in Germany report that, in unencrypted Wi-Fi networks and in networks where all users use the same Wi-Fi key, attackers can potentially use Wireshark to intercept the token and use it for their own purposes.
While third parties have long been able to intercept the app data that is transmitted via unsecured Wi-Fi networks, the token allows potential attackers to gain unauthorised access to users' accounts via the Google API. The problem is not restricted to Google smartphone apps but affects all Android and desktop applications which access the ClientLogin protocol via HTTP instead of HTTPS. According to the researchers, even components such as the Thunderbird plug-in for accessing Google Calendar on a PC are vulnerable if configured incorrectly.
Google has switched the synchronisation of calendar and contact items to HTTPS in Android 2.3.4 and 3, but it has not yet switched the Picasa app, which has been available since 2.3.3. However, the Android team and the app developers are reportedly working on a solution. The researchers at Ulm university recommend that other app developers use HTTPS throughout or switch to the secure OAuth protocol.
While the security problem can, in most cases, be solved by updating to a newer version of Android, such upgrades have yet to become available for many devices. The vulnerable versions 2.1 and 2.2 are installed on an estimated 90 per cent of devices. As a protective measure, users can disable the "auto-sync" feature to prevent the unintended transmission of synchronisation data and tokens when connecting to an unsecured wireless network.
(crve)
![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)
















