Verification protocol
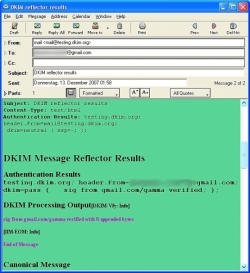
![]() The server replies to emails sent to the dkim-test@testing.dkim.org address with a detailed signature status report.
While most domains send out unsigned emails, a missing or invalid signature in itself is not sufficient evidence for rejecting an email. Therefore, the verification result should be included in the spam score of SpamAssassin. Although SpamAssassin comes with a DKIM evaluation plug-in it also requires the Mail::DKIM Perl module. As with dkim-milter, many distributions contain outdated packages, making it necessary for admins to install the current version using the
The server replies to emails sent to the dkim-test@testing.dkim.org address with a detailed signature status report.
While most domains send out unsigned emails, a missing or invalid signature in itself is not sufficient evidence for rejecting an email. Therefore, the verification result should be included in the spam score of SpamAssassin. Although SpamAssassin comes with a DKIM evaluation plug-in it also requires the Mail::DKIM Perl module. As with dkim-milter, many distributions contain outdated packages, making it necessary for admins to install the current version using the cpan Mail::DKIM command. The installer may offer to install more modules, but this should only be done if these modules are not contained in the respective Linux distribution. To activate the DKIM plug-in, the loadplugin Mail::SpamAssassin::Plugin::DKIM option is set in the version specific /etc/mail/spamassassin/v320.pre configuration file. This option is already included in this file as a comment. The only other thing SpamAssassin needs to know is what to do with messages that contain DKIM signatures. The suitable instructions are valid globally when written into the /etc/mail/spam assassin/local.cf file. It is most effective to give preference to correctly signed emails from known domains. This can be achieved using the whitelist_from_dkim command (see listing below).
| [VERBATIM5] |
As major email senders like eBay still use the outdated DomainKeys method, SpamAssassin should also include these signatures during the transition period.
Several of the major email senders like eBay have not yet switched to DKIM and still use its predecessor DomainKeys. Both Mail::DKIM and the SpamAssassin plug-in can handle both signature types. It is, therefore, sufficient to treat these late bloomers with separate DK rules as shown in our example. Now all that's left to do is determine how a correct signature rates in the spam score (the "spamicity") of a message. SpamAssassin handles this via score entries. The program is already shipped with suggestions the developers optimise by letting their program loose on intercepted spam (and non-spam). At present, a score entry of -100 on the (USER_IN_DKIM_WHITELIST) DKIM whitelist has extremely strong effects; any further spam tests would be pointless. A DKIM verification without whitelist entry, on the other hand, hardly matters at all (-0.001). The reason for this may be that DKIM has so far hardly been used and can, therefore, not be included in the statistics. First practical experiences show that it is safe to shift these weightings. On the author's system, members of the DKIM whitelist only receive a bonus of -4.0 points. Those who aren't explicitly "whitelisted" but sign correctly get 1.3 points deducted from their spamicity. Only those who are still testing DKIM don't receive any special treatment. DomainKeys users are treated in the same way.
Even senders who are known to conform should not be given extraordinarily high scores and, therefore, very easy access. A healthy policy creates well-defined relationships, not unlimited trust. It could well be that the sender suddenly starts to exhibit clear signs of spamming elsewhere, which will then be blanked out completely by one very high scoring DKIM rule. Ultimately, scores are like job applications – the overall impression has to be right. To find out how SpamAssassin rates, save the email to be rated as a file and – as the user who executes SpamAssassin in the mail system – enter on the command line:
spamassassin < emailfile
The X-Spam-Status header contains the tests that were carried out and the overall score. Using a signed and an unsigned email by the same sender is a nice way of reproducing how SpamAssassin's new rules in local.cf apply. DKIM is not in widespread use yet. It has the potential to create much more commitment in everyday emailing – and therefore much more security. Reliable software is available and its implementation is only tolerably complicated. Rules for known communication partners are quickly established so that the invested time pays off.
See also:




![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)












